.png)
Information Security in Project Management Systems: Protecting Your Data and Enhancing Project Efficiency
In the era of digital transformation, where organizations increasingly rely on digital project management systems, sensitive project data has become one of the most valuable—and vulnerable—assets. With the rise of cloud-based platforms and team collaboration tools, the attack surface for cyber threats has expanded. A single breach could expose project plans, financial resources, or client information—undermining stakeholder trust and jeopardizing project success.
To counter these risks, businesses must place information security at the heart of project management. Strong cybersecurity practices ensure that project data remains confidential, accessible only to authorized users, and protected against breaches or misuse. Emphasizing security not only safeguards sensitive information but also builds resilience and long-term credibility.
🚀 In this article, we’ll explore what information security in project management really means, why it’s critical, the key challenges organizations face, and the best practices to strengthen it. Keep reading to discover how your team can manage projects securely while maintaining efficiency and stakeholder confidence.
%20(910%20x%20120%20px)%20(29).png)
Information security in project management systems refers to the set of policies, procedures, and technologies designed to protect sensitive project data from breaches, leaks, or unauthorized access—ensuring the confidentiality, integrity, and availability of information throughout the project lifecycle.
In practice, information security involves identifying potential risks such as unauthorized access or malware attacks and mitigating them through robust security controls. Within digital project management platforms, this translates into:
Ultimately, the goal of information security in project management systems is to protect project schedules, financial resources, and client information from cyber threats—maintaining smooth operations and preserving stakeholder trust.
Information security is critical in project management systems because it safeguards sensitive data, prevents leaks, ensures compliance with regulations, and strengthens stakeholder trust—all of which are essential for project continuity and success.
Key reasons include:
🚀 In short, robust information security transforms project management systems into trustworthy digital environments where organizations can deliver outcomes efficiently and securely.
Information security in project management systems refers to the set of policies, procedures, and technologies designed to protect sensitive project data from breaches, leaks, or unauthorized access—ensuring the confidentiality, integrity, and availability of information throughout the project lifecycle.
In practice, information security involves identifying potential risks such as unauthorized access or malware attacks and mitigating them through robust security controls. Within digital project management platforms, this translates into:
Ultimately, the goal of information security in project management systems is to protect project schedules, financial resources, and client information from cyber threats—maintaining smooth operations and preserving stakeholder trust. 🚀
Information security is critical in project management systems because it safeguards sensitive data, prevents leaks, ensures compliance with regulations, and strengthens stakeholder trust—all of which are essential for project continuity and success.
Key reasons include:
🚀 In short, robust information security transforms project management systems into trustworthy digital environments where organizations can deliver outcomes efficiently and securely.
Digital project management systems face increasingly complex security challenges. As organizations rely more heavily on cloud computing, online tools, and virtual environments, the risk landscape expands significantly.
Some of the most pressing challenges include:
In today’s connected world, these challenges highlight the need for robust security frameworks that combine advanced technology, strict policies, and continuous monitoring to protect project data and maintain stakeholder confidence.
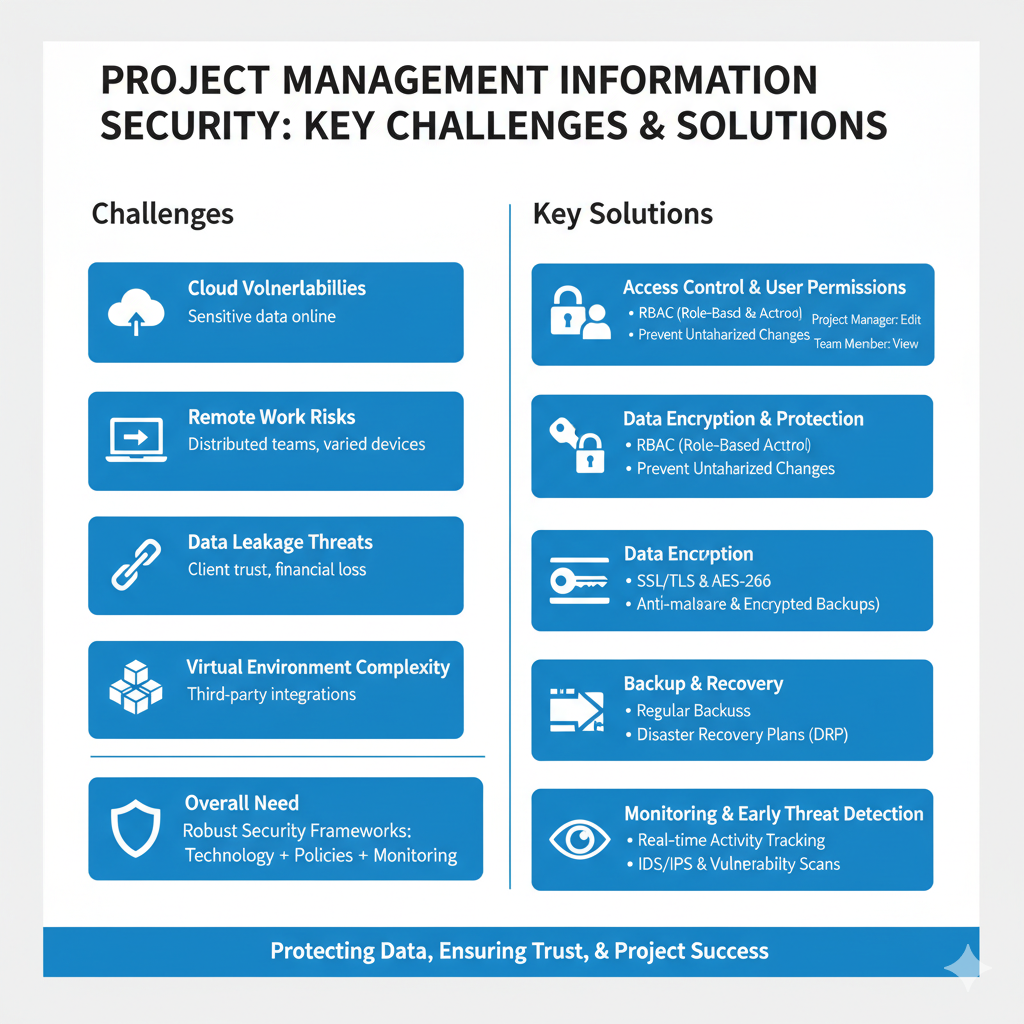
One of the most critical challenges in project management security is defining user permissions with precision. Access control ensures that every member of the system is assigned rights based on their role and responsibilities.
For example:
Technologies such as Role-Based Access Control (RBAC) play a central role in managing who can view, edit, or share project information.
By enforcing strict access control, organizations can:
This structured approach to access and permissions not only protects critical project data but also strengthens accountability and transparency across the entire team.
Encryption is one of the most essential methods for safeguarding project data during both transmission and storage. It transforms information into an unreadable format that can only be deciphered with the appropriate encryption keys.
Modern project management systems must implement:
This ensures that even if unauthorized access occurs, the data remains incomprehensible to attackers.
In addition to encryption, organizations should deploy:
By combining effective encryption with continuous protection measures, companies can create a multi-layered security shield that preserves the confidentiality, integrity, and availability of project information at all times.
Regular data backup is a cornerstone of project information security and business continuity. By creating daily or weekly backups and storing them in separate locations—whether on secure cloud servers or physical media—organizations can quickly restore critical information in the event of a technical failure or a cyberattack that causes data loss.
The value of backup goes beyond safeguarding files; it ensures that projects never lose essential plans, records, or progress reports under any circumstances. To reinforce this, organizations must establish comprehensive Disaster Recovery Plans (DRPs) that clearly define the steps and procedures required to restore systems to full operational status as quickly as possible, with minimal disruption.
Combining regular backups with well-structured recovery strategies creates a powerful security layer, empowering organizations to maintain resilience, safeguard stakeholder trust, and keep projects moving forward—even in times of crisis.
Continuous monitoring serves as the first line of defense against security incidents in project management systems. By tracking login records and suspicious activities in real time, organizations can detect potential breaches or unusual behavior before they escalate into serious threats.
Advanced Project Monitoring Information Systems issue instant alerts whenever anomalies occur—for example, multiple failed login attempts or the sudden export of large volumes of data.
Leading platforms also integrate Intrusion Detection and Prevention Systems (IDS/IPS), along with regular vulnerability scans and penetration tests, to reinforce their security posture. Furthermore, tailored Project Performance Dashboards allow organizations to continuously monitor security while analyzing Security KPIs to ensure controls remain effective.
With this proactive approach, potential attacks are transformed from unexpected surprises into predictable risks—risks that can be anticipated, prepared for, and mitigated before they cause serious damage.
Implementing best practices in information security is essential to protecting sensitive project data, minimizing risks, and ensuring business continuity. The following measures represent the core of a robust security strategy:
Employee Training and Awareness: Educating staff on the importance of strong passwords that combine letters, numbers, and symbols, as well as running workshops on phishing threats, helps close one of the biggest security gaps: the human factor. Regular awareness campaigns significantly reduce accidental data leaks.
Access Permissions Review: Conduct periodic audits of user roles and permissions, removing unnecessary access rights and ensuring each user only has the level of access required for their role. This prevents unauthorized actions and reinforces accountability.
Clear Security Policies: Develop and share documented policies such as system usage guidelines, incident response procedures, and application security rules. Regular software updates and vulnerability checks should also be part of these policies to strengthen system resilience.
Monitoring and Analytics Tools: Leverage intelligent alert systems and interactive dashboards to detect unusual activities in real time—for instance, access attempts outside business hours or from unexpected locations. Early detection enables swift intervention before risks escalate.
Regular Cloud Backups: Maintain routine cloud-based backups to guarantee data recovery under any circumstances. Cloud storage provides fast, reliable restoration from anywhere, ensuring project continuity even during major disruptions.
In conclusion, information security cannot be overstated in project management systems. Any lapse in protection can lead to severe financial losses and long-lasting reputational damage. By applying these best practices, organizations not only secure their data but also strengthen trust, resilience, and long-term success. 🚀
Information security must be treated as an integral part of every stage of the project lifecycle, with controls and preventive measures continuously updated to match the evolution of cyber threats.
By applying the best practices and standards outlined earlier—and ensuring ongoing team awareness—Saudi organizations can safeguard their digital projects while strengthening client and stakeholder trust.
🔹 Discover how the P+ platform can enhance information security, protect your digital assets, and elevate project efficiency with real-time performance monitoring.
🚀 Request your P+ demo today and begin your journey toward safer, smarter, and more efficient project management.
Digital systems offer advanced features such as strong encryption and integrated identity management, making them inherently more secure than traditional methods. However, constant connectivity also introduces new risks. Cybersecurity experts emphasize that the true level of safety depends on implementing robust security controls and policies. Cloud-based solutions, for example, require well-designed protective measures to prevent potential breaches.
Organizations must align with Saudi data protection laws and regulatory frameworks, including:
A secure system must integrate a comprehensive suite of protection measures, such as:
🚀 By combining these measures with ongoing monitoring and compliance efforts, organizations can create a resilient, secure, and future-ready digital project management environment.